Introduction
So this is my first ever VulnHub write-up! It’s probably not the best or most clearly written but we all gotta start somewhere, right??
For my first write-up I’ve chosen Kioptrix Level 1 to keep things simple. (https://www.vulnhub.com/entry/kioptrix-level-1-1,22/)
Start
We first go with nmap to see what we have to work with.
We see that Samba is running on port 139 and we want to dig in a little more. Unfortunately it looks like the version of smbclient that enum4linux uses no longer reports samba version. I’m not sure why it works this way, I haven’t dug into it much yet.
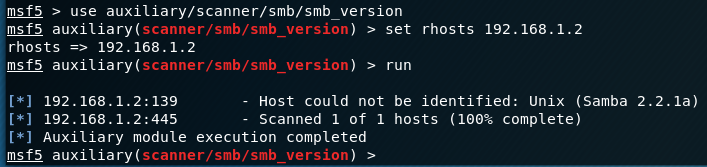
To enumerate the Samba version, we start up Metasploits smb_version scanner.
We see that the machine is running Samba 2.2.1a. A searchspoit search shows nothing for the exact version. Altering the search shows some more options. There are a bunch of Samba 2.2.x exploits we can look at.
Taking a peek at the first 2.2.x exploit shows that it is for a BSD machine. The nmap scan doesn’t seem to indicate BSD so we can skip this one.
Checking the second 2.2.x exploit, we see that it is a generic linux Samba exploit so we decide to try that one.
After doing a quick check of the exploit for any special compiling options or changes we need to make, we see it’s ready to go as is and compile it. Once complied we run it to see the arguments we need to provide. Once we see we just need to provide an IP, we run the exploit.
And we have root! :)
Conclusion
Well, If you’ve made it this far, thank you! Hopefully this wasn’t too painful to read and maybe even somewhat informative! I hope to do more in the future while honing in my documentation and blogging skills.