The stuff I’ve seen around the LOGITacker has had the unit attached to either a computer or mobile device. I wanted to see if I could find a “low cost” setup that could be left behind at an engagement or hidden and accessed remotely. Something that wouldn’t break the bank if it was lost or destroyed.
Equipment
Raspberry Pi Zero w - $10
MakerDiary nRF52840 MDK USB - $12.99
Anker PowerCore 10000 - $25.99 (You can use any powersource, this was small and nearby)
USB OTG adapter - $6.68
Micro SD Card - $10 (Just saying $10 since that’ll get you a decent quality/capacity for this project. I’m using a 32gb that I had)
Total Cost: $65.66
Setup
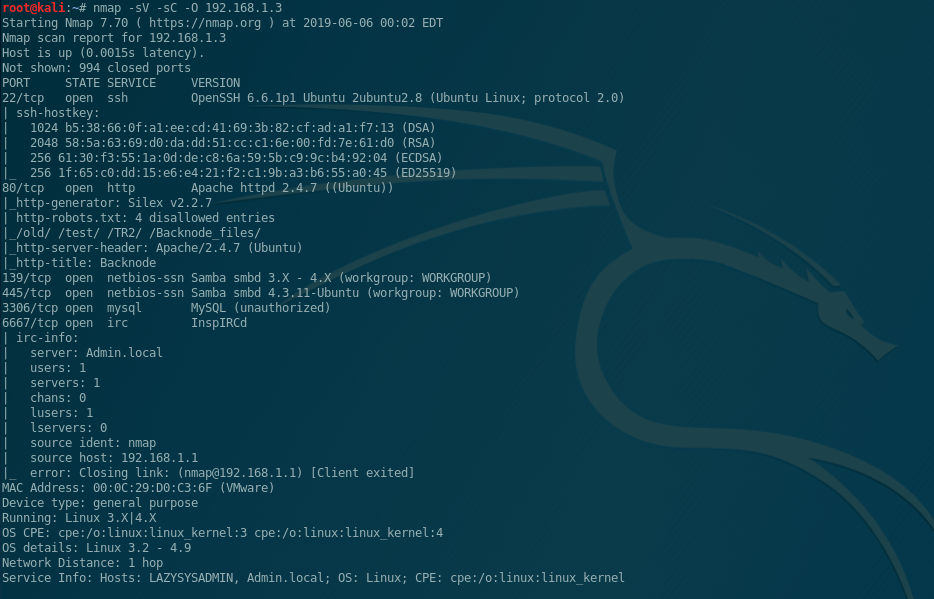
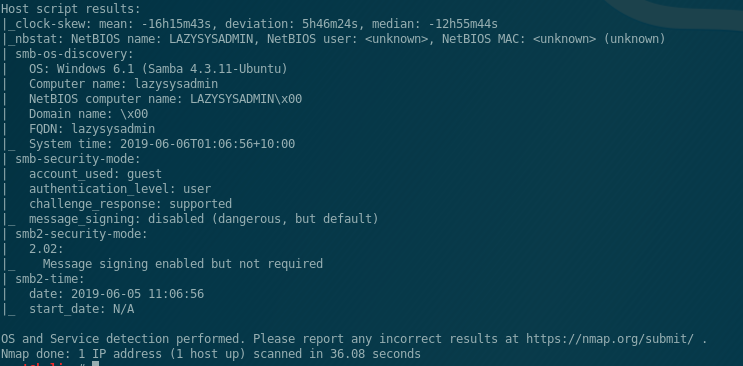
I’m using the standard Raspbian install for the Pi Zero W (https://www.raspberrypi.org/downloads/raspbian/).
I went with “Raspbian Buster with Desktop”. For this setup I put the Pi in AP mode so I’m able to interact with it via it’s WIFI AP. I followed this documentation (https://www.raspberrypi.org/documentation/configuration/wireless/access-point.md) . One item to note, hostapd refused to start for me. Upon reading the logs, I found that it was getting hung up on the line “ignore_broadcast_ssid=0” in the hostapd.conf file. After removing that line and saving, I was able to get the Pi running properly.
If setup following the guide, you should be able to connect to the AP with the SSID/Key that you set. Then start up your SSH client of your choice and SSH to 192.168.4.1. Once connected, you need to install screen (sudo apt-get update) & (sudo apt-get install screen).
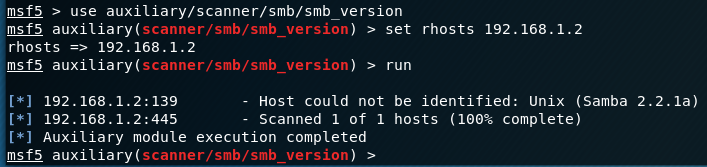
I setup my nRF52840 according to the guide I have here (https://www.jameshickok.com/blog/logitacker-e79n7)
Once everything is up and running, SSH into your Pi and type: screen /dev/ttyACM0
The fun begins!
You should now have remote access to your LOGITacker!
Raspberry Pi Zero W Access Point (AP)
Sniffing decrypted keystrokes from Logitech K400r
Showing currently loaded script
Script ready to execute on Surface Go using Logitech K400r